Quantum Cryptography
Physics Background
The polarization of photons can be thought of as the direction of oscillation of the electric field associated to the light wave \(\vec{E}\). Photons can be represented horizontally, or vertically \(\{\rightarrow, ↑\}\), or diagonally \(\{↗, ↖\}\).
We can encode information using these photons, by polarizing with some filter. We can use one of two bases for this: either the horizontal and vertical base, where we encode ↑ as a logical 1, and → as a logical 0.
Alternatively, we can make use of the diagonal basis, and encode information with ↗ for a logical 1, and ↖ as a logical 0. We then say that we are coding using the basis \(\{ ↗ , ↖ \}\).
To then decode information, we can measure the polarization of each photon with respect to the basis.
Key Distribution
BB84
This is the first key distribution scheme developed by Charles Bennett and Gilles Brassard in 1984. The scheme is as follows: Alice and Bob agree on two representations for ones and zeroes for each basis. This agreement can be done publicly, e.g., \(1 = ↑, 0 = →\) for the \(\{↑, →\}\) basis, then \(1 = ↗, 0 = ↖\) for the \(\{↗, ↖\}\) basis.
Once this has been agreed publicly, then Alice sends a sequence of photons to Bob. Each photon is in a state with a polarization corresponding to a 1 or a 0, but choosing a random basis.
From here, Bob measures the state of the photons received, with each state measured with respect to the randomly chosen basis. Alice and Bob communicate via an open channel. For each photon, they reveal the basis used for encoding and decoding, respectively. Photons which are encoded and decoded with the same basis are kept, whilst those where the basis doesn't agree are discarded.
Say Alice transmits some in the HV (horizontal vertical) basis, and others in the D (diagonal) basis, and Bob randomly selects the basis to decode with. If the basis matches, then this forms part of the key.
This is well illustrated with the following diagram:
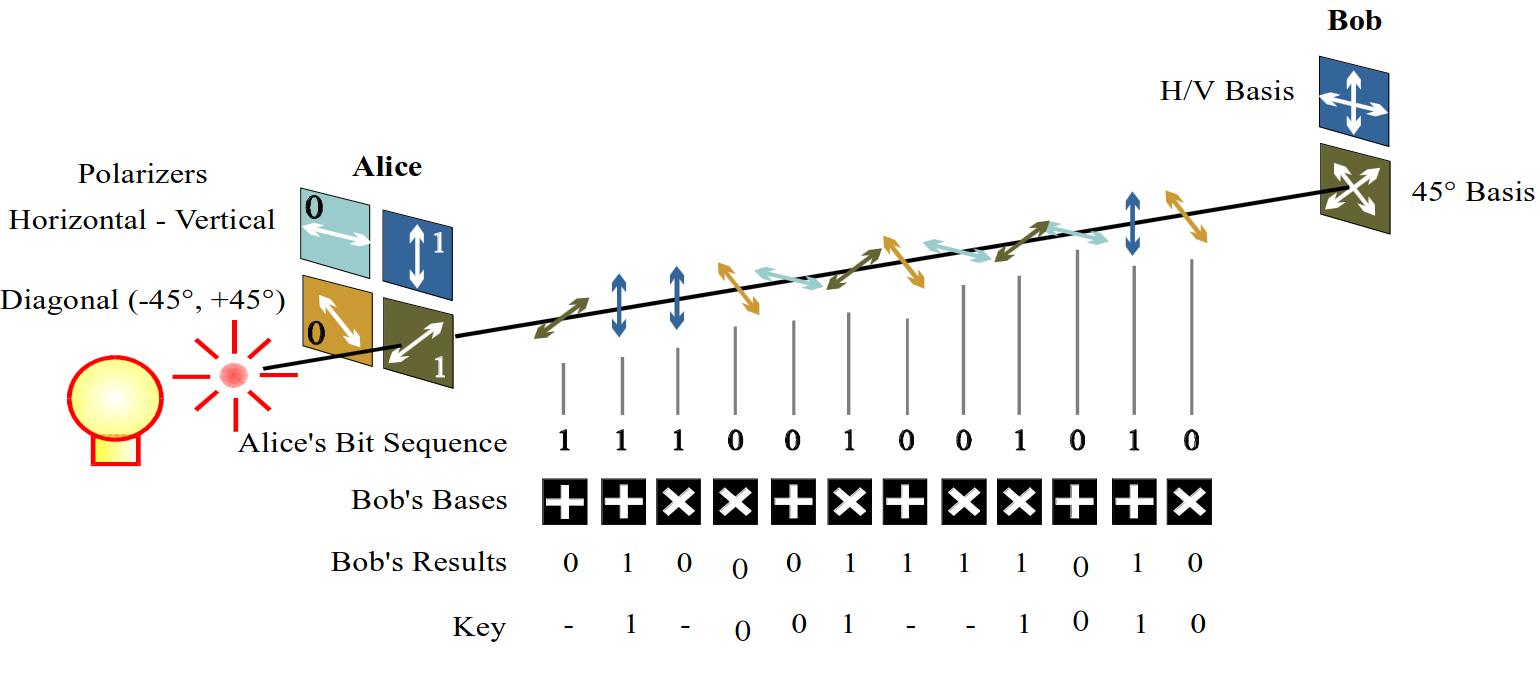
Once this is done, then Alice and Bob need to test the channel for eavesdropping. This can be done if they transmit a random subset of the key, then measure the error rate of the channel.
Eavesdropping
Quantum mechanics fundamentally states that when we measure the two dimensional polarisation, this changes the original polarisation. The measurement of the polarisation not only measures, but transforms the state to one of the basis vectors. This is also the same when we use a diagonal basis.
If the wrong basis is used to measure the polarisation of the photons, then we get an accurate measurement with a probability of 50%. For example, if we try and measure photons polarized with \(\{↗, ↖\}\), but use the \(↑\) filter, then in 50% of cases, we admit the photon, and in 50% of cases, we don't.
Therefore, if we have someone eavesdropping on the conversation, then the error rate of the channel will go way up. Let's introduce Eve, who wants to extract information from this channel (the man- (or more politically correctly) person-in-the-middle), then she needs to measure each photon's polarization.
Whatever basis is picked, Eve will still measure a 1 or a 0. If Eve picks the wrong basis, then there is a 50% chance that she'll get the right value of the bit. This measurement may then change the polarization of the original photon.
The problem lies here, as eve now has to resend all photons to Bob. As Eve doesn't know the correct basis that Alice uses, the eavesdropping will introduce errors, and thus increase the bit error rate of the communications link. We can plot this in a table, with the basis Alice is using, then the basis Eve is using and whether Eve gets it right:
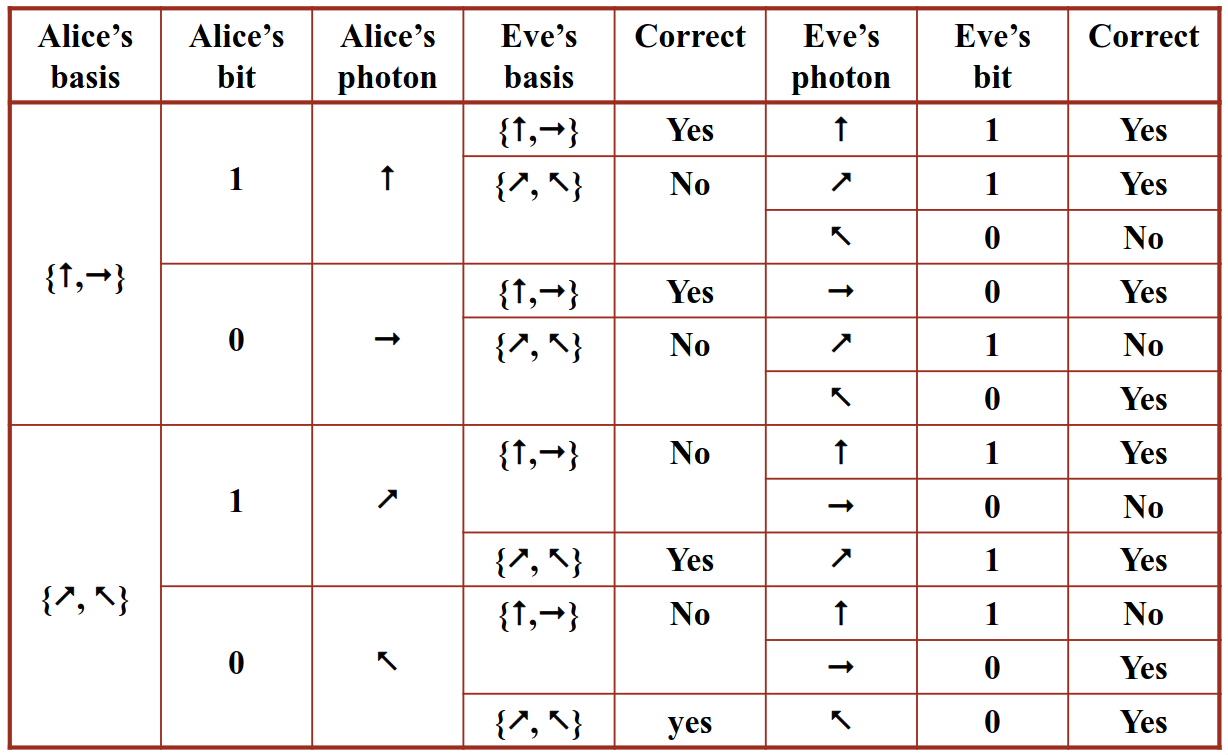
Detection
Once Alice and Bob agree on a key, they then need to test for eavesdropping on the line. They randomly select a number of bits from the key, then calculate an error rate \(E\). If \(E < E_{max}\), then there is no eavesdropping. Otherwise if \(E > E_{max}\), they assume eavesdropping and discard the whole key.
They quantify \(E_{max}\) as the maximum error rate on a particular channel. Eve can still eavesdrop a few photons, but wants to ensure that this doesn't cause the error rate to jump. If Eve does this, then she can have partial knowledge of the key, without raising alarms.